Cardano founder Hoskinson warns against scaremongering about the quantum threat

- The good news: Existing quantum computers cannot break the encryption keys of Bitcoin, Ethereum and other major blockchains.
- The bad news: Future quantum computers can do it – and responsible blockchain operators are already preparing for this today.
Cardano developer Charles Hoskinson recently made several public comments on the topic of threats to blockchain security Quantencomputer. He believes that the real threat posed by quantum computers today is overrated because the crypto industry already knows how to build blockchain systems that are hardened against attacks with quantum computers.
However, systems that could be built with today’s anti-quantum technology are around ten times slower to operate operationally, but at the same time ten times more expensive. Hoskinson therefore warns the industry against activism and premature, possibly wrong decisions.
Nevertheless, some blockchain networks, such as Solana and Aptos, are already testing the integration of quantum-secure encryption systems.
That too US National Institute of Standards and Technology NIST rates quantum computers as one of the most serious future threats to global IT security. The NIST experts emphasize that quantum computers work radically differently than current processor technology and could therefore attack public-key encryption such as RSA and ECC, which are based on factorization and discrete logarithms.
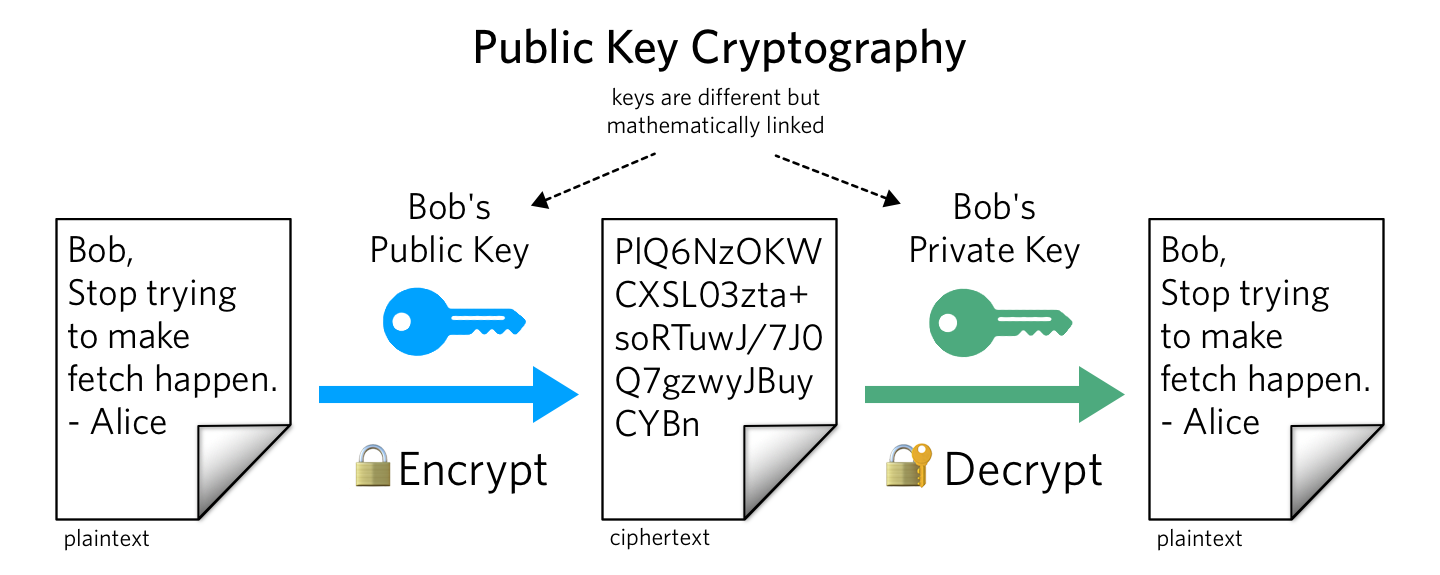
These procedures now secure, among other things, e-commerce, VPN connections, messaging services and identity and certificate infrastructures – highly sensitive areas.
NIST points out that attackers are already intercepting encrypted data in order to later decrypt it using quantum computers. This is seen as a real threat in security policy analyzes that refer to NIST. Data that would have to remain confidential for decades, such as internal government communications, personal healthcare data and intellectual property, is particularly at risk.
NIST responds with new post-quantum standards
As early as August 2024, NIST published three standards for PQS (post-quantum cryptography):
- FIPS 203 – ML‑KEM (Key Encapsulation Mechanism)
- FIPS 204 – ML‑DSA (Digital Signature)
- FIPS 205 – SLH‑DSA (Hash‑based signatures)
The algorithms were developed to withstand attacks from quantum computers and are intended to replace RSA/ECC in the long term.
Complex migration
The NIST experts assume that the process of switching to PQS will take years:
- Hardware, firmware and embedded systems need to be updated
- Certificate infrastructures must be rebuilt
- Software stacks and protocols need upgrades
- Interoperability must be guaranteed in all of this
Companies should therefore start inventorying their cryptographic systems and planning migration paths early on.








No Comments